Authenticated Encryption (AE) are forms of encryption which simultaneously assure the confidentiality and authenticity of data.
Programming Interface
A typical programming interface for an AE implementation provides the following functions:
- Encryption
- Input: plaintext, key, and optionally a header in plaintext that will not be encrypted, but will be covered by authenticity protection.
- Output: ciphertext and authentication tag (message authentication code or MAC).
- Decryption
- Input: ciphertext, key, authentication tag, and optionally a header (if used during the encryption).
- Output: plaintext, or an error if the authentication tag does not match the supplied ciphertext or header.
The header part is intended to provide authenticity and integrity protection for networking or storage metadata for which confidentiality is unnecessary, but authenticity is desired.
Motivation
The need for authenticated encryption emerged from the observation that securely combining separate confidentiality and authentication block cipher operation modes could be error prone and difficult.
Approaches
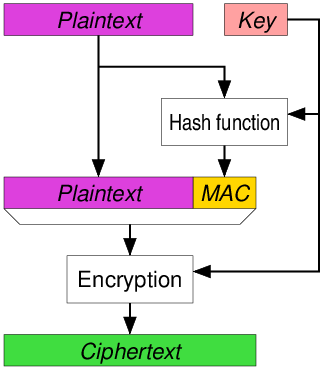
Encrypt-then-MAC (EtM)
The plaintext is first encrypted, then a MAC is produced based on the resulting ciphertext. The ciphertext and its MAC are sent together.
Used in IPsec.
This is the only method which can reach the highest definition of security in AE, but this can only be achieved when the MAC used is “strongly unforgeable”.
Note that key separation is mandatory (distinct keys must be used for encryption and for the keyed hash), otherwise it is potentially insecure depending on the specific encryption method and hash function used.
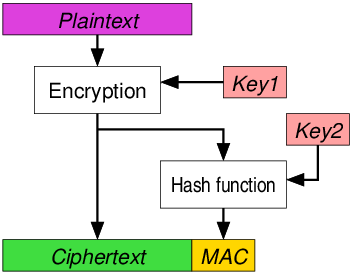
Encrypt-and-MAC (E&M)
A MAC is produced based on the plaintext, and the plaintext is encrypted without the MAC. The plaintext’s MAC and the ciphertext are sent together.
Used in, e.g., SSH.
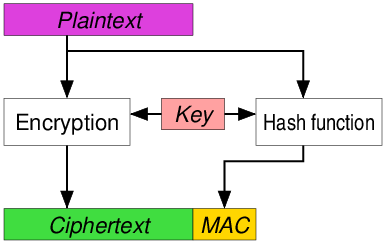
MAC-then-Encrypt (MtE)
A MAC is produced based on the plaintext, then the plaintext and MAC are together encrypted to produce a ciphertext based on both. The ciphertext (containing an encrypted MAC) is sent. AEAD is used in SSL/TLS.[16] Even though the MtE approach has not been proven to be strongly unforgeable in itself,[13] the SSL/TLS implementation has been proven to be strongly unforgeable by Krawczyk who showed that SSL/TLS was, in fact, secure because of the encoding used alongside the MtE mechanism.